Azure Virtual Desktop (AVD) is a cloud-based desktop as a service (DaaS) solution offered by Microsoft Azure. It provides access to a virtualized Windows environment, allowing users to run applications, access data, and store files in the cloud.
With the rising need for flexible computing solutions, the virtual desktop infrastructure market is growing at a Compound Annual Growth Rate of 19.2% during the forecast period (2022–2030) (GlobeNewsWire 2022). As a result, AVD is becoming increasingly popular.
While the trend indicates that this industry is booming, it also means that it will be an easy target for cyber-attacks. It becomes important for us to reinforce our infrastructure’s security backbone and avoid taking any shortcuts. Security and networking are two critical aspects when it comes to AVD.
Build up your AVD Security
The security of data and applications is of utmost importance when using any cloud-based service. Organisations that adopt a cybersecurity network architecture by 2024 will reduce the financial liabilities of security breaches by 90% (Gartner 2022).
AVD relies on Microsoft Azure’s security infrastructure, which includes physical security, network security, and data protection. The service also uses encryption to protect data in transit and at rest, ensuring that sensitive information remains confidential.
Multi-factor authentication
Multi-factor authentication (MFA) is another important feature of Azure Virtual Desktop. MFA adds an extra layer of security by requiring users to provide a second form of identification, such as a one-time code sent to their phone, in addition to their username and password. This helps prevent unauthorized access to the virtual desktop environment and the data stored there.
Role-based access control
Role-based access control (RBAC) is another security feature of Azure Virtual Desktop. RBAC allows administrators to restrict user access to sensitive resources, ensuring that only authorized individuals have access to sensitive information. This helps minimize the risk of data breaches and unauthorized access to sensitive data.
Improve accessibility with AVD
Networking is another critical aspect of AVD. The service uses Microsoft Azure’s global network infrastructure, which provides low latency and high availability. This helps ensure that the virtual desktop environment is accessible and responsive, even when users are accessing it from remote locations.
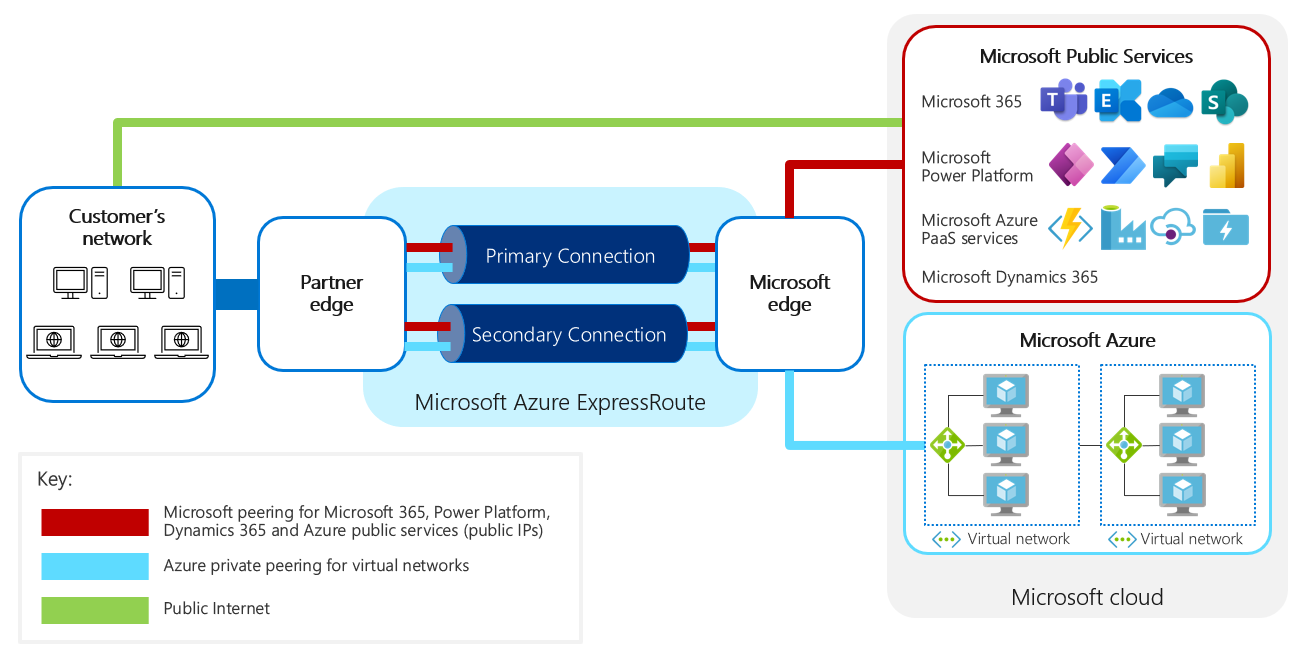
Azure ExpressRoute
However, the performance of AVD will depend on the quality of the user’s internet connection. A fast and stable internet connection is essential to ensure the best possible performance. If network connectivity is an issue, Azure ExpressRoute can be used to establish a private connection between the user’s on-premises infrastructure and the Azure Virtual Desktop service.
ExpressRoute provides an additional layer of security by allowing users to bypass the public internet, reducing the risk of data breaches and unauthorized access. ExpressRoute also provides a more stable and predictable network connection, helping to ensure that Azure Virtual Desktop is always accessible and responsive.
Secure Remote Access with AVD
In conclusion, AVD is a secure and convenient solution for remote work and on-the-go computing. With the security and networking features provided by Microsoft Azure, users can be confident that their data and applications are protected and accessible when they need them. The use of encryption, MFA, RBAC, and ExpressRoute helps ensure that sensitive information remains confidential and that the virtual desktop environment is accessible and responsive. If you are considering using Azure Virtual Desktop, be sure to take these important security and networking considerations into account.
Join our Panel Discussion event to get all the best AVD networking and security tips straight from the experts. We’ll be joined by speakers from Microsoft, Nerdio, and cubesys as they run you through fundamental concepts as well as what network isolation has achieved for our clients. If you miss the live event, check out the event replay.