When BitLocker is enabled on a Windows device, the recovery key can be saved to Azure Active Directory (Azure AD), a USB, a file, or even printed. End-users can access this key for their owned device through Azure AD or by going to their device properties.
If you don’t know how to access it through Azure AD, first go to Azure AD and then click on the Devices blade. From here, you can access the BitLocker keys (Preview).
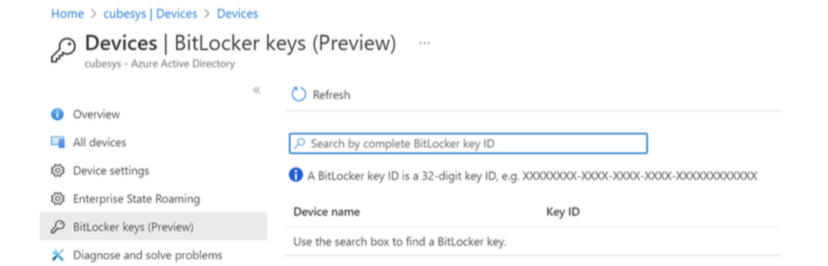
Restricting access to the BitLocker recovery key in Azure
First, you need to make sure that you’ve updated your authorisation policy to turn off the self-service BitLocker key access, which can be done using the Microsoft Graph PowerShell module.
|
|
Once this authorisation policy has been updated, the following Azure AD roles will be able to access they key:
- Global administrators
- Security administrators
- Intune Service administrators
- Security readers
- Any custom role with the right permissions