Introduction to Network Security Perimeter
Network Security Perimeter is a powerful feature offered by Microsoft Azure that allows organisations to define a logical network isolation boundary for Platform-as-a-Service (PaaS) resources. This feature is particularly useful for securing resources such as Azure Storage accounts and SQL Database servers that are deployed outside your organisation’s virtual networks. By restricting public network access to these resources, Network Security Perimeter ensures that only authorized traffic can reach your PaaS resources.
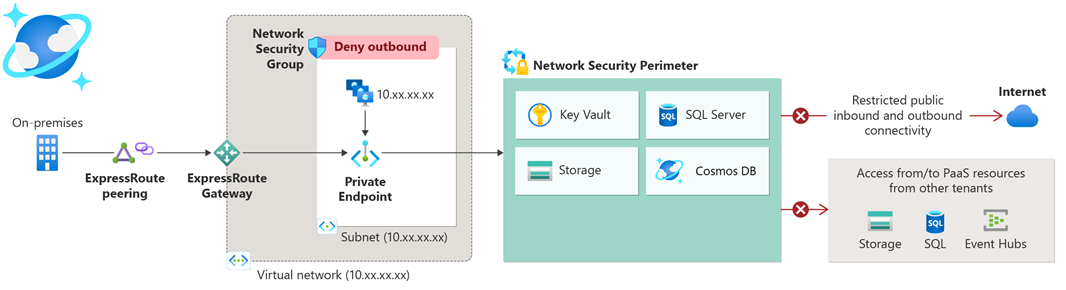
Detailed Step-by-Step Implementation Guide Using Bicep
Create a Network Security Perimeter
Open Azure CLI: Start by opening your terminal and logging into your Azure account using az login.
Create a Resource Group: Create a new resource group where your Network Security Perimeter will reside.
|
|
Create the Network Security Perimeter: Use Bicep to define and deploy the Network Security Perimeter.
|
|
Deploy the Bicep Template: Deploy the Bicep template using the Azure CLI.
|
|
Associate Resources with the Perimeter
Add Resources to the Perimeter: Associate your PaaS resources with the Network Security Perimeter.
|
|
Configure Access Rules
Define Access Rules: Add inbound and outbound access rules to control network access.
|
|
Deploy the Updated Template: Deploy the updated Bicep template.
|
|
Limitations
Its worth noting the below limitations for this feature
| Limitation | Description |
|---|---|
| Number of network security perimeters | Supported up to 100 as recommended limit per subscription. |
| Profiles per network security perimeters | Supported up to 200 as recommended limit. |
| Number of rule elements per profile | Supported up to 200 as hard limit. |
| Number of PaaS resources across subscriptions associated with the same network security perimeter | Supported up to 1000 as recommended limit. |
Conclusion
Implementing Network Security Perimeter using Bicep is a straightforward process that significantly enhances the security of your PaaS resources. By following the steps outlined above, you can create a secure network isolation boundary, control access to your resources, and ensure compliance with your organisation’s security policies.